2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
In recent years, the decentralized finance (DeFi) space has witnessed a dramatic increase in both participation and, regrettably, hacking incidents. With approximately $4.1 billion lost to DeFi hacks in 2024 alone, ensuring that your assets remain safe is more critical than ever. The rise of sophisticated cyber threats highlights the necessity for platforms to adhere to robust security standards, such as HIBT. This comprehensive guide will delve into the HIBT under framework within the broader context of blockchain security, focusing on the essential practices for safeguarding your digital assets.
Understanding the HIBT Framework
The HIBT under security standards represent an advanced set of protocols aimed at bolstering the security of blockchain platforms. These standards are designed to address vulnerabilities prevalent in smart contracts, consensus mechanisms, and wallet security, among other areas. By adopting the HIBT guidelines, crypto platforms can enhance their defense mechanisms against potential security breaches.
Key Components of HIBT Security Standards
- Robust smart contract auditing procedures
- Secure wallet management practices
- Advanced consensus algorithm evaluations
- Comprehensive incident response strategies
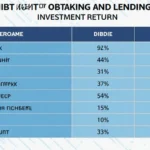
A recent survey highlighted that around 73% of crypto users are concerned about the safety of their assets, emphasizing the importance of HIBT-compliant platforms.
Vulnerabilities in Consensus Mechanisms
Blockchain technology leverages various consensus algorithms to maintain the integrity of the network. However, vulnerabilities exist, similar to how a bank vault can have hidden weaknesses. For instance, proof of work (PoW) mechanisms are often considered robust but can be susceptible to 51% attacks, where a single entity gains control over the majority of mining power.
Enhancing Consensus Security
To mitigate these vulnerabilities, platforms must implement layer two solutions and hybrid consensus models, combining both PoW and proof of stake (PoS) elements for enhanced security. By doing so, they can significantly reduce attack vectors.
Smart Contract Audit Necessities
Smart contracts are the backbone of decentralized applications (dApps). Unfortunately, many contracts are prone to bugs and vulnerabilities. Reports indicate that about 60% of hacks targeting DeFi platforms in 2024 involved flaws in smart contracts.
Best Practices for Auditing Smart Contracts
- Incorporate thorough testing phases using test networks
- Engage third-party auditors with a history of successful audits
- Employ formal verification methods to guard against logical errors
Platforms like HIBT are crucial in providing reliable audits that assure users and investors of contract integrity.
Cryptocurrency Wallet Security
Your wallet is where your digital assets reside, making its security paramount. Traditional wallets can be ideal for fewer transactions but can easily become a security risk when mismanaged. Given that over 40% of crypto losses in 2024 stemmed from wallet hacks, users must prioritize wallet security.
Recommended Wallet Security Practices
- Use hardware wallets for substantial holdings
- Enable two-factor authentication (2FA) on all wallet accounts
- Regularly update wallet software to patch vulnerabilities
According to recent statistics, user adoption of hardware wallets in Vietnam surged by 150% in the last year, indicating a growing awareness of security practices.
The Role of User Education in Security
While technology provides various security measures, user education remains vital. Many hacks can be traced back to user error, such as sharing private keys or falling prey to phishing attacks.
Effective User Education Strategies
- Regularly conduct security awareness webinars and training
- Provide clear, straightforward resources on best security practices
- Utilize gamification to encourage learning among users
By ensuring users are informed, platforms can significantly enhance overall network security.
Cutting-Edge Solutions for Enhanced Security
Blockchain platforms continuously innovate to shield users from evolving threats. Strategies like decentralized identity solutions and machine learning are increasingly employed to recognize and counter potential risks.
Future Innovations in Blockchain Security
Emerging technologies, such as Artificial Intelligence (AI) in security monitoring, are anticipated to redefine how vulnerabilities are detected and addressed:
- AI can analyze patterns and identify anomalies swiftly.
- Blockchain’s inherent transparency facilitates real-time auditing.
- Integration of biometric security measures can strengthen access control.
As of 2025, it will be crucial for users and developers alike to stay abreast of these innovations in order to enhance security.
Conclusion: Adopting HIBT Standards for Secure Blockchain Transactions
In a world where digital assets are becoming increasingly valuable, adopting stringent security measures backed by frameworks like HIBT is essential. By embracing these standards, platforms can not only protect their users but also build trust and credibility within the crypto community. As we look towards 2025, adhering to security practices will be a cornerstone for success in the blockchain space.
With appropriate strategies in place, users can confidently navigate through the complexities of digital asset management, minimizing risks of potential hacks and theft. Always ensure to consult reliable sources and platforms like HIBT for your security needs.
Let’s work together to build a more secure cryptocurrency ecosystem as we inch closer to the future. Brand awareness and security practices will be key in shaping this new digital landscape.